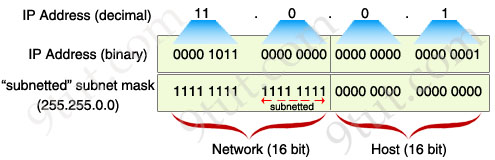
One important thing we should notice is that a valid subnet mask must have all bit “1″s and “0″s successive, in which bit “1″s must be on the left; bit “0″s must be on the right. Therefore we only have 8 situations:
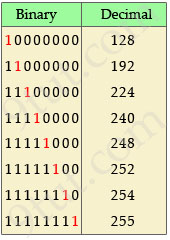
Table 2 – lists all valid subnet masks
This is a very important table to do subnet quickly! Please take some time to learn it by heart. Make sure you remember the right-most bit “1″ position (the least significant bit 1, which are in red in the above table) and their equivalent decimal values.
In most cases, this table is used to quickly convert a number from decimal to binary value without any calculation. For example, you can quickly convert the 4th octet of the subnet mask 255.255.255.248 to 11111000. Or if you are given a subnet of /29 you will know it equals to 255.255.255.248 (by thinking “/24 is the default subnet mask of class C so /29 will have the right-most bit “1″ at 5th position).
Try to practice with these questions:
+ “/28″ in binary form?
+ “255.255.224.0″ in binary form?
+ “255.192.0.0″ in slash notation form?
+ “/26″ in binary form?
+ “255.128.0.0″ in binary form?
+ “248.0.0.0″ in slash notation form?
(Please try to solve by yourself before reading the solution)
Answers:
+ /28 -> 1111 1111.1111 1111.1111 1111.1111 0000
+ 255.255.224.0 -> 1111 1111.1111 1111.1110 0000.0000 0000
+ 255.192.0.0 -> /10
+ /26 -> 1111 1111.1111 1111.1111 1111.1100 0000
+ 255.128.0.0 -> 1111 1111.1000 0000.0000 0000.0000 0000
+ 248.0.0.0 -> /5
How to find out the increment number?
The increment is the heart of subnetting; if you can find out the increment, you can find all the information to solve a subnetting question. So it is usually the first thing you must find out in a subnetting question.
The increment number is the number specifying how “big” your subnets are. Let’s take an example of the increment number! Did you remember the subnets in “Exercise 3″ in the previous part? By changing bits in the Network part, we found out 4 subnets:
+ First subnet: 198.23.16.0/30 (the 4th octet is 00000000)
+ Second subnet: 198.23.16.4/30 (the 4th octet is 00000100)
+ Third subnet: 198.23.16.8/30 (the 4th octet is 00001000)
+ Fourth subnet: 198.23.16.12/30 (the 4th octet is 00001100)
In this case the increment is 4 (in the 4th octet) because the “difference” between two successive subnets is 4 (from 0 -> 4; from 4 -> 8; from 8 -> 12)
There are 2 popular ways to find out the increment number:
1) Use the formula:
In which “x” is the first octet (counting from the left) which is smaller than 255 in a subnet mask. For example:
+ In a subnet mask of 255.224.0.0 -> x = 224
+ In a subnet mask of /29 -> x = 248 (because /29 = 255.255.255.248)
+ In a subnet mask of 1111 1111.1111 1100.0000 0000.0000 0000 -> x = 252
In the case you see a subnet mask of 255.255.255.255 (which is very rare in CCNA), x = 255
Note: Also remember which octet “x” belongs to because we have to plus the increment to that octet.
Now let’s solve Exercise 3 again by using this formula:
Exercise 3 one again (with the formula 256 – x):
Your company has just been assigned the network 198.23.16.0/28. How many subnets and hosts-per-subnet you can create with a subnet mask of 255.255.255.252?
The subnet mask is 255.255.255.252 -> x = 252 (x belongs to 4th octet)
Therefore the Increment = 256 – 252 = 4
The initial network 198.23.16.0/28 is also the first subnet, so:
+ The first subnet: 198.23.16.0/30
+ The second subnet: 198.23.16.4/30 because the increment is 4 so we plus the network address with it to get the next network address (0 + 4 = 4)
+ The third subnet: 198.23.16.8/30 (4 + 4 = 8)
+ The fourth subnet: 198.23.16.12/30 (8 + 4 = 12)
Note: We know there are only 4 subnets because we borrow 2 bits.
2) Learn by heart the decimal value of the rightmost bit “1″ in the subnet mask:
Another way to find the increment value is to write “x” in binary: 11110000. Consider the rightmost bit “1″, the decimal value of this bit is the increment value. In this case it equals to 16.
The table below summarizes the decimal values of bit “1″ depending on its position. To use this method, you should learn by heart this table:

Table 3 – How to find out increment based on the “least-significant” (rightmost) bit 1
Now let’s solve Exercise 3 again by using this method:
Exercise 3 one again (with the “decimal value of the rightmost bit 1″ method):
Your company has just been assigned the network 198.23.16.0/28. How many subnets and hosts-per-subnet you can create with a subnet mask of 255.255.255.252?
First use Table 2 to convert 252 to 1111 1100. The decimal value of the rightmost bit “1″ is 4 (according to Table 3) -> The Increment is 4.
After finding out the increment we can deduce 4 subnets it creates.
The initial network 198.23.16.0/28 is also the first subnet, so:
+ The first subnet: 198.23.16.0/30
+ The second subnet: 198.23.16.4/30 because the increment is 4 so we plus the network address with it to get the next network address (0 + 4 = 4)
+ The third subnet: 198.23.16.8/30 (4 + 4 = 8)
+ The fourth subnet: 198.23.16.12/30 (8 + 4 = 12)
Note: We should only choose one method to use and try to practice, practice & practice more with it. Practice until you can solve any subnetting questions within 20 seconds!
Maybe you will ask why 256 can help you find the increment. In fact, by using the formula Increment = 256 – x you are trying to separate the rightmost bit “1″ from other bits:
256 – x = 255 – x + 1
In which “255 – x” will convert all bit “0″s to bit “1″s and all bit “1″s to “0″s while “+1″ part will make our result have only one bit “1″ left. For example, if x = 240 then:

So in fact we can say two above methods are the same!
Resource:- http://www.9tut.com/